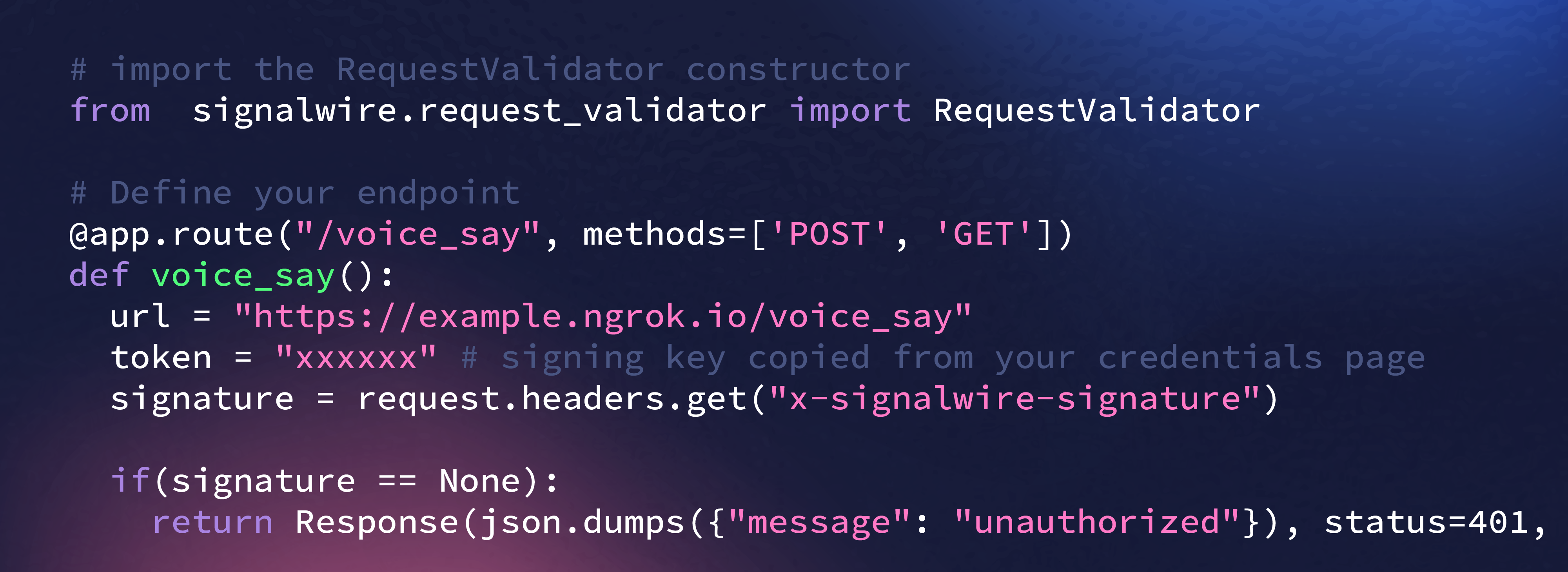
Encryption Without Exceptions
All communication and data are encrypted by default using protocols that exceed industry standards, regardless of the channel or device.
TLS 1.2/1.3 for encrypted signaling across HTTP, SIP, and websockets
SRTP + DTLS for voice and video
AES-256 and RSA-4096 encryption for storage
Secure transmission across HTTPS and encrypted websocket channels
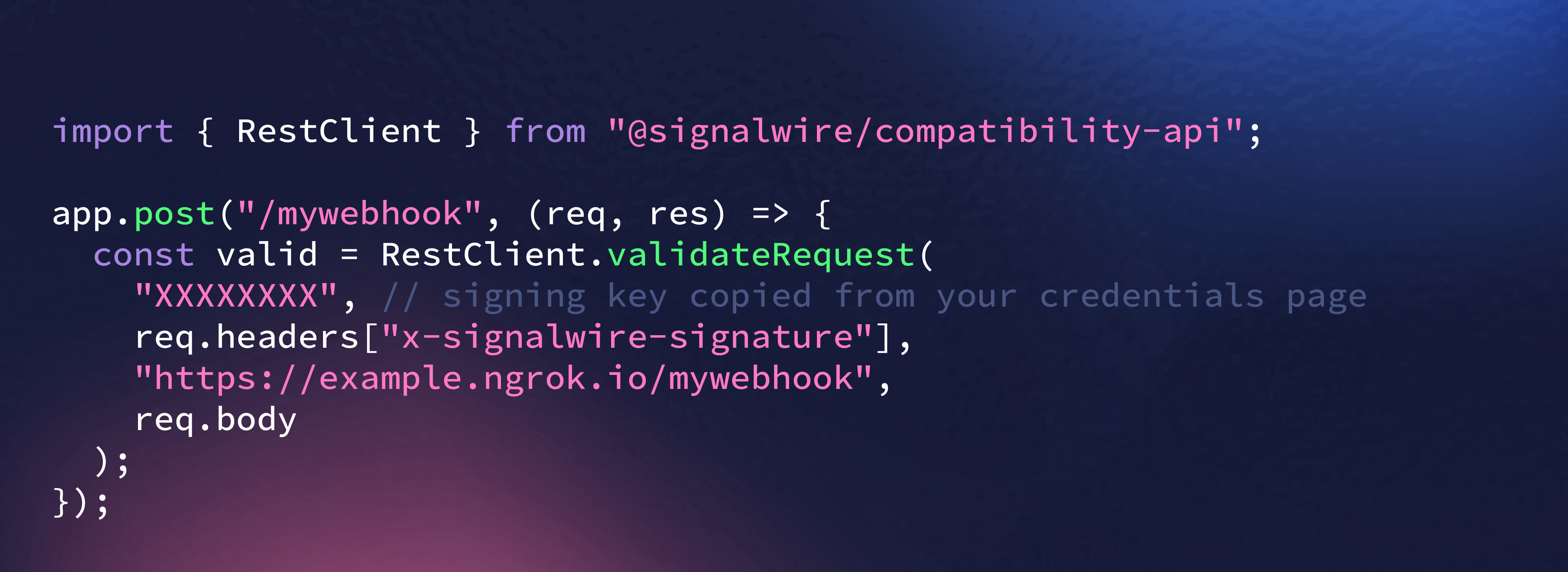
Continuous Threat Detection
We continuously monitor, test, and improve our platform to detect vulnerabilities early and respond before they become threats.
Static and dynamic code analysis in the CI/CD pipeline
Real-time intrusion detection with automated alerting
Continuous vulnerability scanning and behavior analytics
Third-party penetration tests and independent security audits
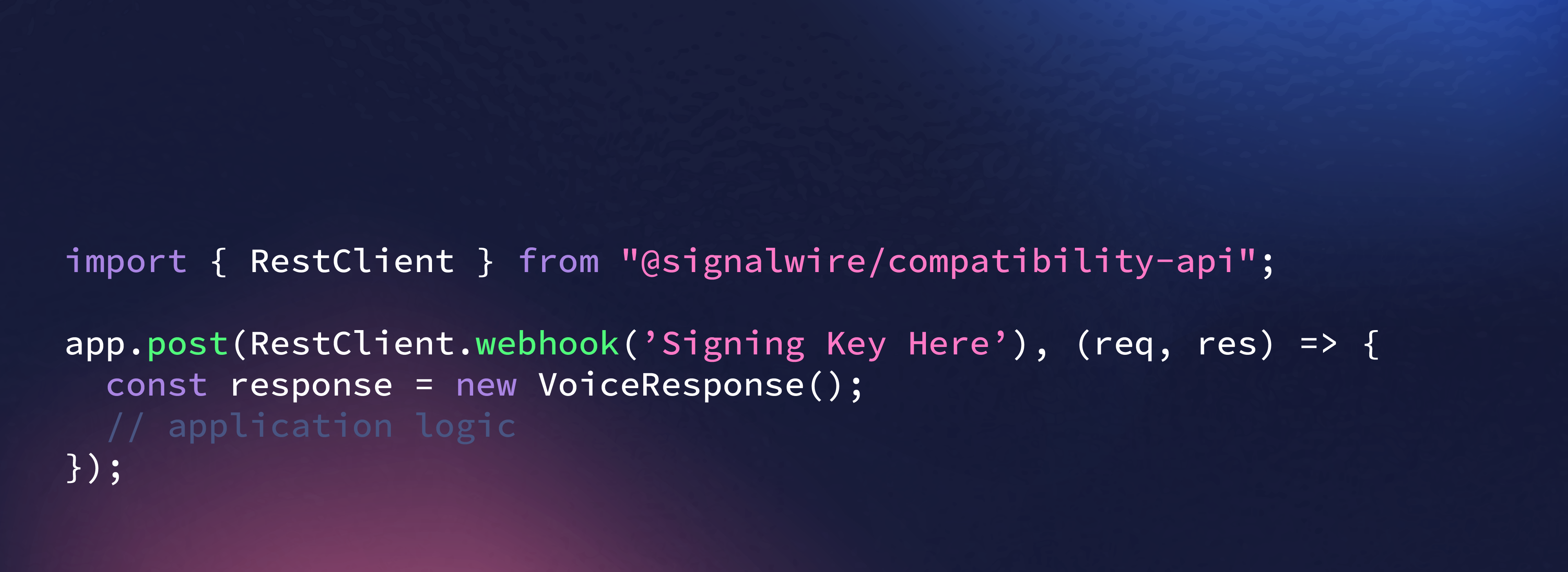
Isolation By Design
Our infrastructure is built to limit exposure by default. We separate workloads, restrict access, and enforce strong authentication across all systems.
Isolated environments for voice, video, messaging, and AI services
Scoped credentials for every application and integration
Role-based access control with two-factor authentication (2FA)
Fine-grained permission management for internal and external tools